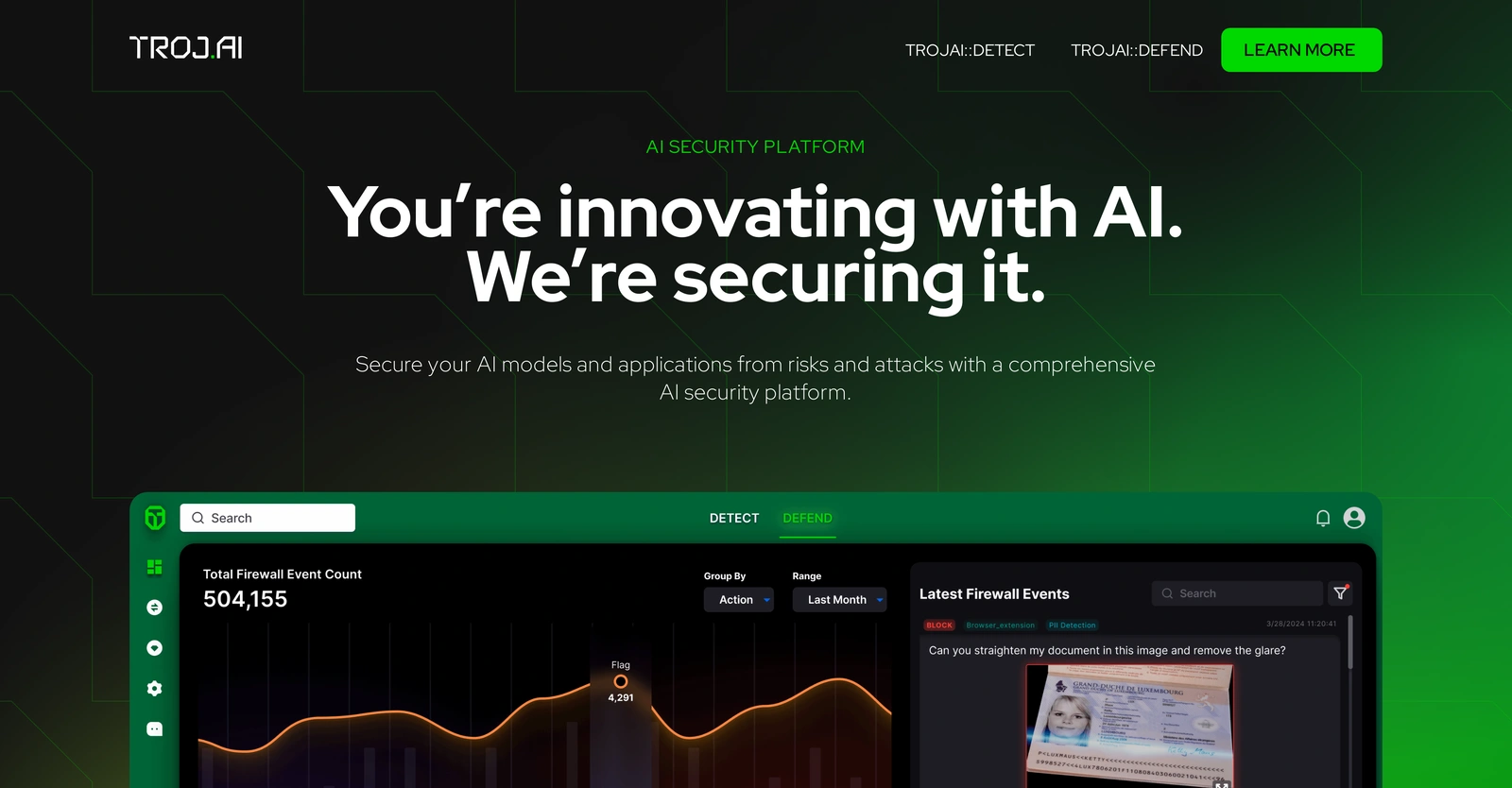
TrojAI is a specialized platform designed to enhance the security of Artificial Intelligence (AI) models and applications by mitigating risks and potential threats. The platform comprises two essential components: TrojAI::DETECT and TrojAI::DEFEND. TrojAI::DETECT seamlessly integrates with AI and MLOps workflows to conduct automated penetration testing of AI models prior to deployment, enabling organizations to proactively detect concealed risks and vulnerabilities. This process ensures a seamless integration of AI technologies while maintaining compliance standards. TrojAI::DEFEND provides real-time protection against potential attacks through a rules engine supported by data science principles. Moreover, it facilitates the secure utilization of public AI services by monitoring and filtering inbound and outbound traffic, thereby preventing unauthorized access and ensuring auditing capabilities. Furthermore, the platform assists organizations in navigating intricate regulatory frameworks and standards pertaining to AI, thereby facilitating compliance adherence without impeding the pace of AI adoption. By conducting thorough model testing before deployment, TrojAI helps prevent potential data breaches and safeguards sensitive information during the application deployment phase.
Description
Get to know the latest in AI
Join 2300+ other AI enthusiasts, developers and founders.
Thank you!
You have successfully joined our subscriber list.
Add Review
Pros
Activity auditing capabilities
Automatic penetration testing
Complex regulatory navigation assistance
Inline with OWASP Framework
Optimized for MLOps workflows
Pre-deployment vulnerability detection
Prevents data poisoning
Prevents sensitive data loss
Proactive vulnerability detection
Protection from data loss
Solution for prompt injection
Automatic penetration testing
Complex regulatory navigation assistance
Inline with OWASP Framework
Optimized for MLOps workflows
Pre-deployment vulnerability detection
Prevents data poisoning
Prevents sensitive data loss
Proactive vulnerability detection
Protection from data loss
Solution for prompt injection
Cons
Lack of customization options
Lacks individual user auditing
Limited integration options
No automated threat updating
No confirmed global support
No disclosed data source
No indication of performance speeds
No support for model explainability
Opaque operation procedures
Restricted to pre-production testing
Lacks individual user auditing
Limited integration options
No automated threat updating
No confirmed global support
No disclosed data source
No indication of performance speeds
No support for model explainability
Opaque operation procedures
Restricted to pre-production testing
Alternatives
Promote Your AI Tool
Get seen by thousands of AI enthusiasts, founders & developers.
- Homepage, Search and Sidebar Ads
- Featured Placements
- Click Stats & more
AI News









Leave a Reply